Experienced – Talented – Professional
What is IoT?
The Internet of things (IoT) describes the network of physical objects—“things”—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the Internet.
Things have evolved due to the convergence of multiple technologies, real-time analytics, machine learning, commodity sensors, and embedded systems.Traditional fields of embedded systems, wireless sensor networks, control systems, automation (including home and building automation), and others all contribute to enabling the Internet of things. In the consumer market, IoT technology is most synonymous with products pertaining to the concept of the “”smart home””, including devices and appliances (such as lighting fixtures, thermostats, home security systems and cameras, and other home appliances) that support one or more common ecosystems, and can be controlled via devices associated with that ecosystem, such as smartphones and smart speakers. IoT can also be used in healthcare systems.
There are a number of serious concerns about dangers in the growth of IoT, especially in the areas of privacy and security, and consequently industry and governmental moves to address these concerns have begun including the development of international standards.
The Internet of things (IoT) describes the network of physical objects—“things”—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the Internet.
Things have evolved due to the convergence of multiple technologies, real-time analytics, machine learning, commodity sensors, and embedded systems.Traditional fields of embedded systems, wireless sensor networks, control systems, automation (including home and building automation), and others all contribute to enabling the Internet of things. In the consumer market, IoT technology is most synonymous with products pertaining to the concept of the “”smart home””, including devices and appliances (such as lighting fixtures, thermostats, home security systems and cameras, and other home appliances) that support one or more common ecosystems, and can be controlled via devices associated with that ecosystem, such as smartphones and smart speakers. IoT can also be used in healthcare systems.
There are a number of serious concerns about dangers in the growth of IoT, especially in the areas of privacy and security, and consequently industry and governmental moves to address these concerns have begun including the development of international standards.
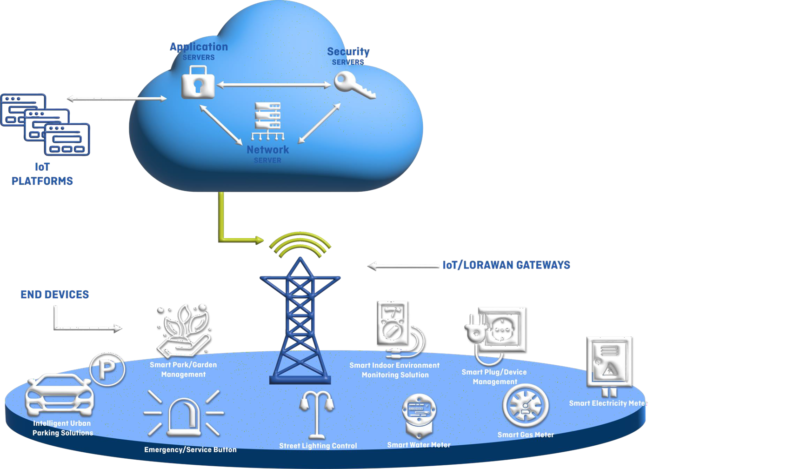
IoT Architecture
IoT system architecture, in its simplistic view, consists of three tiers: Tier 1: Devices, Tier 2: the Edge Gateway, and Tier 3: the Cloud. Devices include networked things, such as the sensors and actuators found in IIoT equipment, particularly those that use protocols such as Modbus, Bluetooth, Zigbee, or proprietary protocols, to connect to an Edge Gateway. The Edge Gateway layer consists of sensor data aggregation systems called Edge Gateways that provide functionality, such as pre-processing of the data, securing connectivity to cloud, using systems such as WebSockets, the event hub, and, even in some cases, edge analytics or fog computing.Edge Gateway layer is also required to give a common view of the devices to the upper layers to facilitate in easier management. The final tier includes the cloud application built for IIoT using the microservices architecture, which are usually polyglot and inherently secure in nature using HTTPS/OAuth. It includes various database systems that store sensor data, such as time series databases or asset stores using backend data storage systems (e.g. Cassandra, PostgreSQL). The cloud tier in most cloud-based IoT system features event queuing and messaging system that handles communication that transpires in all tiers. Some experts classified the three-tiers in the IIoT system as edge, platform, and enterprise and these are connected by proximity network, access network, and service network, respectively.
Applications
Experienced – Talented – Professional
How to Prepare Networks for IoT
In most installations, their networks were already in place before IoT was introduced. When reconsidering network security, it’s good to review what vulnerabilities still need to be addressed, as well as what prepares the network for integrating IoT devices. There are a few things to consider before adding or creating an IoT environment for any setting:
Upgrade the network to get higher bandwidth.
The influx of endpoints will take resources that a network cannot provide. Failure to account for the increase in IoT devices added to the network and constantly exchanging data can cause connectivity issues in the future. Companies should plan ahead to best allocate bandwidth, specifically, to determine which areas will need more and when. Check existing endpoints on the network. Before users add IoT devices or create an IoT environment, they should also check the security of the devices that are part of the network. Endpoints such as computers or smartphones can be weak connections, especially if these devices are relatively old or have missed important updates. These endpoints should also be checked for compatibility with new devices that will be added to the network, as monitoring for potential compatibility issues can help manage these additions.
Keep network policies up to date.
Businesses also need to prepare and update their network policies. Employees of a business that is constantly on the network must always be aware of the impact of more endpoints being added to the network. Therefore, updated network policies should include new security requirements such as user authorization management, “bring your own devices” (BYOD) rules, and work from home (WFH) policies.